Recently, several readers asked me to define the various internet webs, i.e., the surface, deep and dark webs; terms that are often used in an interchangeable, and wrong, manner. In this article, we also provide information on updated law enforcement task force formation to combat dark web crime, and avenues to monitoring the dark web for personal and professional data breaches, by professional services or by yourself.
First, the three main webs defined:
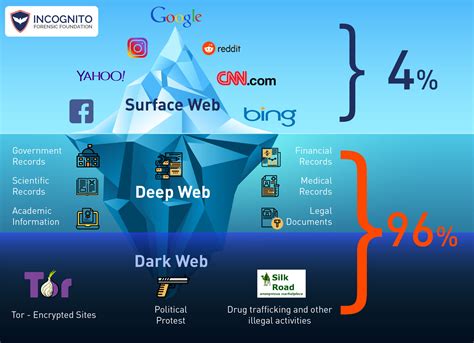
Succinctly,
Surface Web: The majority of people employ Google, Bing, Firefox, Safari and like browsers. That area of the internet is called the surface or open web. It is the tip of internet that is visible to all, if you liken the internet to an iceberg. The surface web comprises only 4% of the entire Internet.
Deep web: The deep web is the portion of the Internet that is hidden and not shown from conventional search engines. IOW, it cannot be accessed by search engines; harboring sensitive and private information such as government data, bank data, cloud data (think the content of your personal email and social media accounts), etc. To access deep web data, you must go to the website, log in and locate the information within the site. Journalists and politically oppressed people internationally are common inhabitants of this space. The NYT has a permanent lockbox on this web.
Dark Web: The dark web, a subset of the deep web, refers to heavily encrypted online content that is not indexed by conventional search engines. Access requires a password, encryption, or specialty software to surf the anonymous environment as well as as a multi-layered encryption browser, i.e., TOR. This is where law enforcement concentrates its focus in that this is the area of the web in which criminals and nefarious routes reside (e.g. the Silk Road black market).
From the National Institute of Justice:
The criminal side of the dark web relies on anonymizing technology and cryptocurrency to hide its trade in an assortment of contraband such as opioids and other drugs, bomb parts, weapons large and small, child pornography, social security numbers, body parts — even criminal acts for hire.
The dark web’s anonymity not only encourages illegal activities, it keeps many law enforcement agencies largely unaware of its existence, even while their jurisdictions are impacted by online transactional crimes.
What is Law Enforcement Doing About The Thriving Dark Web Marketplace?
Law enforcement recognizes the burgeoning darkweb criminal ecosystem and has responded by forming a joint task force specifically to monitor the black market of money laundering, illegal drug sales and child pornography distribution, to name several targeted dark web crimes. See the press release of April, 2023: U.S. Attorney and Federal Law Enforcement Partners Announce Formalization of Darknet Marketplace and Digital Currency Crimes Task Force
Can I Monitor Myself or My Business?
We suggest reading this beginner’s primer from CrowdStrike on dark web monitoring before you make a decision to hire a dark web monitoring service. Before hiring a service, you may want to check yourself for instances of data breach exposure(s) tied your email address or phone number through a free search on haveIbeenpwned.com. If you find your personal data has been breached, reach out to us and let’s determine a tailored approach. To be blunt, not every instance of data breach requires correction in that its impact may be negligible- almost everybody who’s been online for any considerable period of time (which is most of us) will find their email or phone number floating around the dark web. However, if you believe you or your company may have been compromised in any way, there are definitive steps that may be taken to neutralize or minimize potential personal or professional reputation or operational damage.
The above provides a glimpse into the enormous scope of the internet that domestic and foreign law enforcement agencies must monitor. By the sheer size of the web, unless one is labeled a potential master criminal or terrorist, law enforcement is mostly reactive in monitoring people. One would have to commit egregious criminal acts over a prolonged period of time for deep, sustained monitoring. (I say this knowing that, as I referred to the above task force, AI long-term monitoring tools have been developed and are being refined as I type. Lots to keep an eye on here.)
BNI Operatives: Situationally aware.
As always, stay safe.